Security practices for providers of essential services in Luxembourg
While the world is becoming more resource-constrained, globalised and urbanised, governments and organisations seek more efficient and smart solutions in responding to shifts in preferences and expectations. The new waves of technology — the Internet of Things (IoT), Artificial Intelligence (AI), robotics, virtual reality and sharing economy platforms — are taking existing products and services to a new level. Just in recent years, investor funding in AI has risen nearly sevenfold, from 45 million USD in 2010 to 310 million USD in 20151. Across industries, the widespread rollout of robotics is already underway, with spending expected to reach 67 billion USD annually by 20252.
The intense advance of technologies has been an ongoing research topic. Three themes — intelligent, digital, and mesh — form the basis for the Top 10 strategic technology trends for 20173 according to Gartner Top 10 Strategic Technology Trends. Pointing out these trends such as advanced machine learning, intelligent apps, blockchains, conversational systems, digital technology platforms, and adaptive security architecture, the report implies digitisation of the World to be experienced by individuals, organisations and governments.
EY, in its recent research4, has outlined three root causes of the global transformative trends which are technology, globalisation, and demographic change. These main forces define the present and shape the future by their impact on businesses, economies, industries, societies and individual lives. Different types of innovations based on technologies and new business models, are altering consumption patterns and are ubiquitous in day-to-day activities from health care to education and banking.
In the light of the accelerated pace of progressive technologies, the number and cost of security incidents and data breaches continuously increase. The most recent researches internationally demonstrate steady growth of data breaches cost and the severity of impact caused by them with malicious or criminal attacks being the prevailing root of these breaches. According to the research conducted by Ponemon Institute5 involving 383 companies from 12 countries, the average total cost of data breach increased by 29% since 2013 and reached 4 million USD in 2016 while the average cost per lost or stolen record increased by 15% since 2013 and amounted to 158 USD.
The component of the 4 million USD cost of data breach
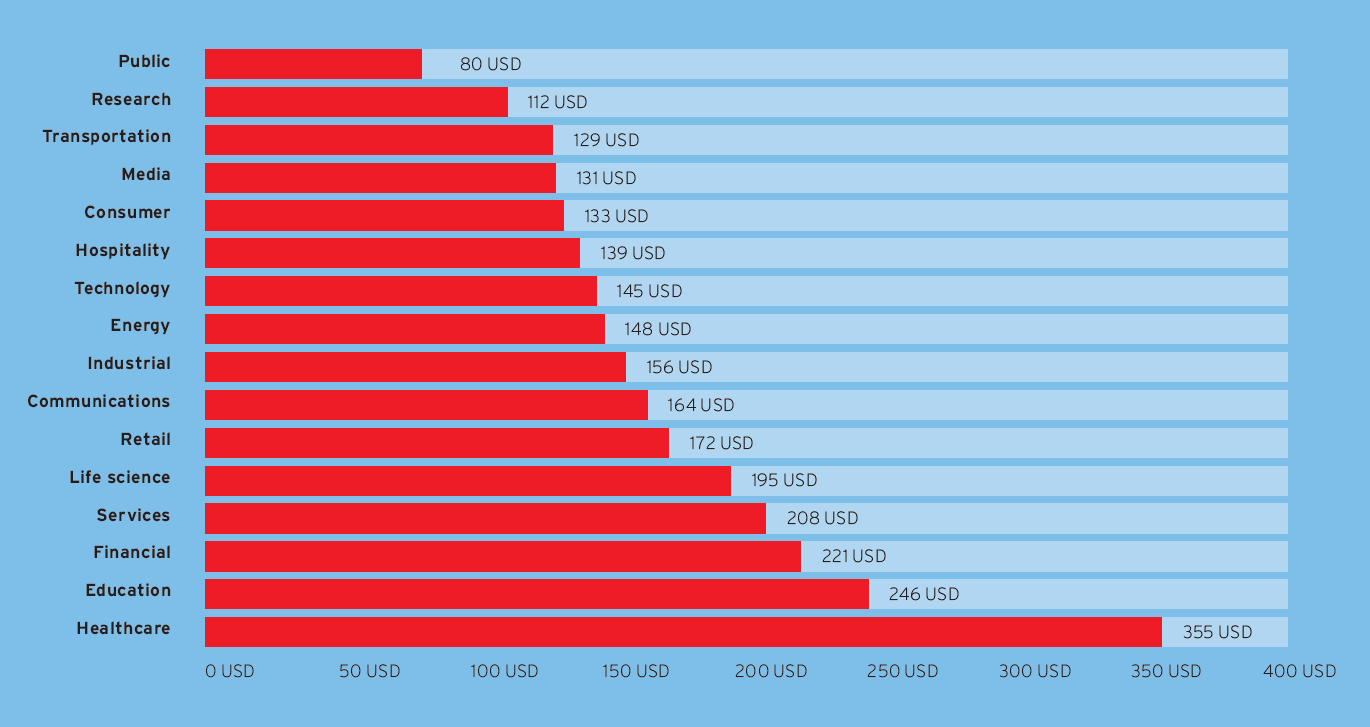
The cost of data breach per record varies by industry and is higher for heavily regulated sectors such as healthcare, education and finance because of fines and the higher than average rate of lost business and customers.5

Cost per record by industry classification, measured in USD
Over recent years and under the pressure of more regulation, organisations have invested in their corporate shield. Significant progress has been made in taking measures to strengthen this shield and in the last two to three years, organisations focus more on their capabilities of detection and escalation. Most organisations, however, are lagging behind in preparing their reaction to a breach, still ignoring the all-too-familiar statement, “it’s not a matter of ‘if’ you are going to suffer a cyber-attack, it’s a matter of ‘when’ (and most likely you already have…).” The statement is constantly justified as even the most notorious incidents have led to a sensational data leakage involving world famous companies all around the globe.
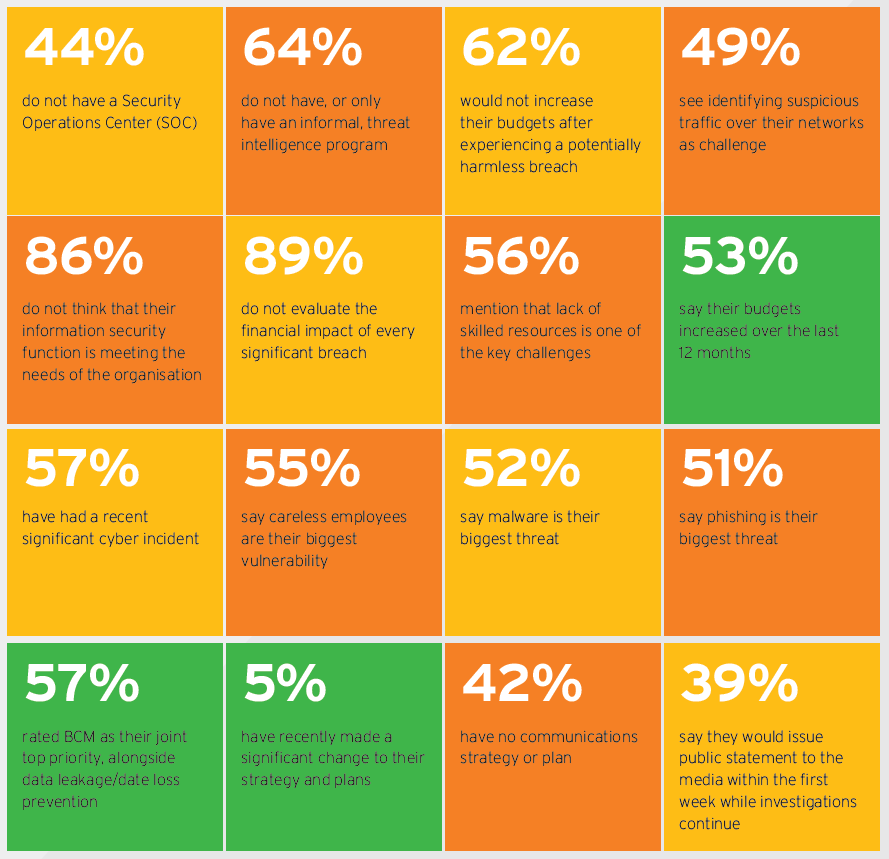
According to EY’s most recent Global Information Security Survey6 over the last two years, 87% of board members and C-level executives have said that they lack confidence in their companies’ level of cybersecurity. Further results of the survey are presented below.
Indicative results of the 2016 EY Global Information Security Survey
According to the latest European study on digital transformation by the European Commission7, the Grand Duchy occupies an honourable 6th place based on the Digital Transformation Enablers’ Index (DTEI). Luxembourg is considered to be one of top-10 most digitized countries8 worldwide together with countries such as Japan, Norway, Sweden, Finland, the Netherlands, Switzerland and Singapore. The assessment is based on the Network Readiness Index (NRI) and has been conducted for 139 countries which “measures the capacity of countries to leverage Information and Communications Technologies (ICTs) for increased competitiveness and well-being with consideration to recent innovation trends through the lens of NRI”.
Even for a country being so profound in ICTs, there are still areas to be attained to and cybersecurity is one of the highest priority among them. This is constantly justified through occurring security incidents and breaches, an example of which is the most recent successful attack on the state’s internet infrastructure. Overall in 2016, there were over 120,000 events and 900 incidents registered which led to approximately 4,000 special investigations9.
Public initiatives for Cyber resilience in Luxembourg
Considering the abovementioned, it is natural that cybersecurity initiatives in Luxembourg are continuing to grow. Currently, there are various organisations which work with each other at country level to address the different dimensions of cybersecurity. One of them is GOVCERT.LU – the Computer Emergency Response Team of the Luxembourg government, whose role is to manage incidents related to the governmental information systems and critical infrastructures, coordinates with the Cybersecurity Board (CSB) of Luxembourg. One of the purposes of this collaboration is to provide a national cybersecurity policy, strategy and roadmap which are up-to-date and address the security needs of the governmental organisations within the country.
Similarly, another service of the Ministry of Luxembourg, Computer Incident Response Centre Luxembourg (CIRCL), which is a comparable country initiative. It is also designed to ensure review, report and respond to computer security threats and incidents as well as provide a dependable and trustworthy point of contact for anyone wishing to report security incidents for communes, non-governmental organisations or the private sector. It offers classes to its members and shares field experience through a set of trainings and technical courses.
Establishments such as the Cyber World Awareness and Security Enhancement Services (CASES) play a significant part in promoting activities to create awareness and communicate best practices on the subject of security. In addition to this, and even if several pre-existing services have already been present in Luxembourg, as of February 2015, the country has further increased open communication and transparency among the different players.
With the advent of Security Made in Luxembourg (SMILE), Luxembourg is now equipped with a single and centralised online source of information, guidelines, best practices and news for those interested and involved in cybersecurity initiatives. The goal of SMILE is to also provide a toolbox with useful cybersecurity solutions for private users, organisations and the wider ICT community. One evident measure, which has been taken as a result of SMILE, is that of utilising a common Malware Information sharing platform. The platform allows users to share threat indicators with each other among the private and public sector.
Finally, FEDIL, The Voice of Luxembourg’s Industry, has been working for many years now on actively contributing to several initiatives in Luxembourg, mainly for organisation of the industrial sector. It provides support to members in all kinds of areas notably in cybersecurity.
FEDIL-ICT and EY Cybersecurity annual studies
The cybersecurity study10 conducted by FEDIL – ICT and EY in 2016 aimed at providing organisations and companies in Luxembourg, guidance on adopting a common approach in regards to security objectives, security requirements and security measures. At the core of the study, 10 security domain areas have been covered combining both a strategic and operational direction:
- Cybersecurity Strategy: Awareness, People competencies, Framework security, Risk and Assurance, Design and Architecture, and
- Cybersecurity Operational: Data Protection and Privacy, Identity and Access Management, Continuity and Resilience, Threat Management, and Technology Protection.
The study was directed at the providers of essential services in Aerospace industry, Aviation, Banking, Healthcare, Power and Utilities, Public sector, Telecommunication and Startups. For the purpose of the study, security and business stakeholders provided their opinions on the security areas out of suggested 10 key domains.
The analysis was performed through a series of interviews with different organisations. The first step was to identify the participants who could provide the most pertinent insight. This was done by contacting relevant panelists (such as CIO’s, CISO’s CTO’s) of the biggest players of the strategic industries in Luxembourg. Afterwards series of interviews were conducted based on a set of 50 practice rules which were derived from common security standard frameworks (such as ISO270001, BSI C5, NIST and COBIT 5). Based on the inputs collected from these interviews and the available resources, an analysis was performed in order to identify which key players were leading in particular disciplines and the areas in which further development was required. Consequently, specific aim and requirements in the form of 50 security practices have been described for each of the areas to be reached by the organisations wanting to excel in bringing their cybersecurity to the highest level according to global best practices and specific industry standards. These were grouped in 10 areas and can be described as the following:
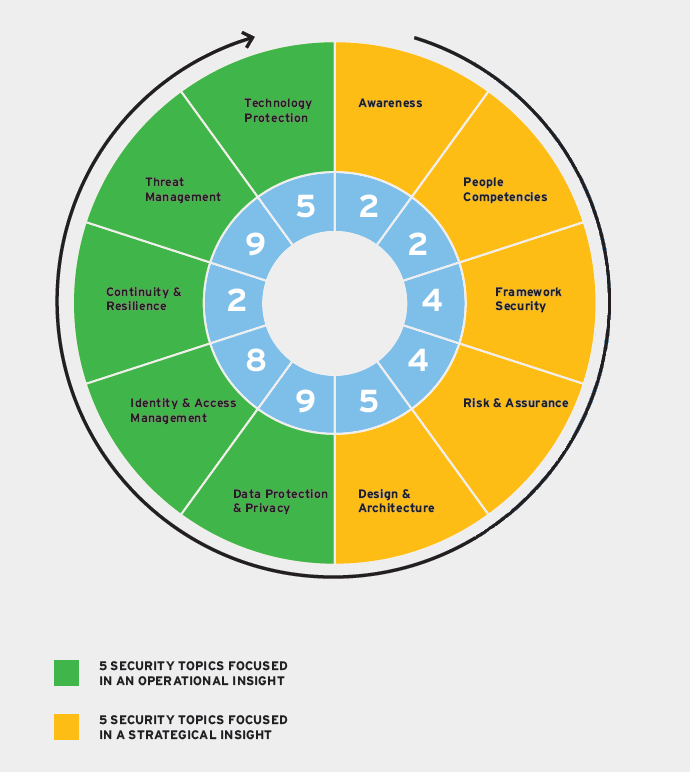
- Awareness about practice rules of security and regular trainings for staff, including specific trainings on technical aspects for IT and IS staff,
- People Competencies should be developed and maintained, relying on Chief Information Security Officer (CISO) and a qualified workforce of IT security professionals,
- Security Framework is essential for each organisation moving towards IS enhancement. Thus, organisations with support of the top-management should retain a set of IS policies and procedures and perform regular assessments of IT and IS,
- Risk and Assurance implies a regular monitoring and reporting on IS functions as well as risk management activities,
- Security Architecture implies maintaining high-risk profile devices and critical information assets together while performing dedicated technical reviews and audits and enforcing relevant policies and procedures on the practice of bringing your own device (BYOD), remote access and software management,
- Data Protection and Privacy is about identification of a high-valued data and data classification as well as establishing relevant privacy procedures and controls,
- Identity and Access Management prescribes the rules and procedures for logical and physical access management involving passwords management, user and privileged accounts control and handling,
- Continuity and Resilience involves conducting Business Impact Analysis (BIA) along with adopting a strategy for business continuity and disaster recovery,
- Threat Management requires the establishment of a comprehensive incident management process and implementation of a proactive threat treatment approach,
- Technology Protection involves adopting a set of technical controls and measures in order to provide security for network, operation systems and applications.
Another important part of the study was to perform a maturity assessment of the respondents in the 10 defined areas, conducted based on two key functional aspects which made up the questionnaire.
As key outcomes of more than 50 interviews performed with panelists, the majority of sectors have reached the minimum standard level. Nonetheless, while we expected some security fields, like “Awareness” or “Data Protection and Privacy”, to be ones of the most covered topics, for most respondents, we observed that capabilities of the majority of companies are slightly behind.
Also, in view of Luxembourg’s ambitions to develop the ICT sector, cybersecurity is becoming a strategic pillar to enable the digital transformation of the country. From that perspective, it is worthy to note the good positioning of startups and ICT companies in the cybersecurity landscape.
Data Protection and Privacy is a trend topic and benefits from a very disparate coverage level in Luxembourg. We noted that certain sectors, where data protection is a main component of the core business, were in the leading position on that matter. Technological evolution and increasing amount of manipulated data will lead to important challenges on Identity Access Management and Technology protection (e.g. encryption, digital signature, etc.) in the coming years. Indeed, we observed also a correlation between the capability to invest in R&D and the level of maturity in the field of technology protection.
Also, Threat Intelligence and vulnerability management are growing topics but still a new field in the Luxemburgish environment, as reflected in the results of our interviews. It is worthy to note a real effort among all panelists to reinforce their capabilities in Cyber threat management, in alignment with evolution in European regulations (e.g. Directive NIS, Regulation 910/2014/EU – Electronic identification and trust services for the electronic market, 8/2014).
The results on the category “Functional capabilities” also reflect a satisfying commitment and sponsorship at the top-management level given that cybersecurity is now on the top of the agenda of boards and C-level meetings.
Nevertheless, all of the companies interviewed agree on the fact that it is currently really complicated to find out new talents in cybersecurity (private, public, advisory, companies) and that it is now crucial to set specific talent and training programs in order to meet the decision-makers expectations and sustain cybersecurity challenges over the years.
Our collaborative study has shown that while Luxembourg is on a steep progression towards improvement of security measures, and even if it has led to continuous positive outcomes, more collaboration among the different stakeholders and an augmented level of standardisation in the security measures is welcomed bearing in mind the need to address each business’s specific needs.
Following these observations, and thanks to intended sectorial initiatives led by key public representatives such as SMILE and the Ministry of the Economy with its new Cybersecurity Competence Center (C3) which will pave the way of providers of essential services in their cybersecurity journey, we can conclude that Luxembourg is now organised to strengthen its security footprint and to become a key player in that field. In order to succeed in standing up from the crowd, all actors need, starting from now, to keep Luxembourg Cybercommunity living and continue to share and enrich the catalogue of best practices.
Still, with respect to this, another FEDIL initiative supported by EY has been launched. This will be exposed in the form of a collaborative tool designed to share security practice rules via an online assessment which would produce dynamic feedbacks and recommendations for the online participants.
FEDIL-ICT Cybersecurity Awareness Increase Initiative
The uniqueness and importance of the initiative impose specific demands to the capability, usability and support of the tool thus bringing up the following requirements:
- Accessible for any company in the Grand Duchy
- Dynamic assessment of the maturity against practice rules and/or companies of the same sector/same size
- Profound file/data maintenance options in terms of usability and data processing
- Integration with other data processing packages for alternative display and reporting facilities
- Flexible reporting tools with standard layouts and options for their customisation
- Appropriate user support and explicit FAQs
- Multi-year follow up of data
- State-of-the-art in terms of security and data protection
- Flexible anticipated workplace environment while easily accessible and user-friendly
The assessment will be carried out for the willing organisations in several steps, which may be described as following:
- Determining the business profile and completing some basic information about the company (e.g. approximated revenue, number of employees, main industry). This is necessary in order to perform benchmarking only with comparable organisations.
- Choosing a focus point out of proposed security areas depending on the nature of company’s industry and core of business as well as maturity level.
- Answering the questionnaire. On each of the selected security areas, a set of questions will be proposed allowing to evaluate the maturity level of the organisation. This estimated maturity will be then compared with companies having the same characteristics.
- Setting the objectives and desired future state. Based on the position among company’s peers a maturity objective would be set. The tool will provide a description of best practices, an action plan and some relevant material to achieve the desired objective.
With all that, FEDIL intends to build a strong and solid solution enabling comprehensive and easily accessible aid for the organisations and companies in Luxembourg in raising their cybersecurity awareness. This is going to be the 1st Cyber tool for Luxembourg built in a collaborative way with the main providers of essential services of the country, also aligned with a National Cybersecurity Strategy and Digital Luxembourg initiative. It’s a new opportunity for adopting a nationwide benchmarking against peers and sharing experience and lessons learnt in terms of reinforcement of a digitized and secure country brand through the promotion of security practice rules.